Social media and entertainment accounts sold illegally are now carving out their niche in Dark Web marketplaces.
This report describes the trends and prices of illegally sold hacked social media and entertainment accounts.
Gathered from the dark web from January 2022 to January 2023, the account values show several effects of supply and demand–and the fact that no one is safe from cybercrime.
Summary: The dark web has become a marketplace for hacked social media and entertainment accounts, with LinkedIn accounts being the most expensive at $45, and Reddit accounts being the cheapest at $6. From January 2022 to January 2023, we observed that no social media platform is safe from cybercrime. With hacked accounts readily available for sale, it is crucial to discuss and implement strategies to avoid becoming a victim of these illegal activities.
This is what we found:
| Type | Hacked service | Price |
|---|---|---|
| Social Media | $45 | |
| $14 | ||
| Discord | $12 | |
| $12 | ||
| Snapchat | $11 | |
| $10 | ||
| $9 | ||
| TikTok | $8 | |
| $6 | ||
| Communication | Gmail | $45 |
| $18 | ||
| Zoom | $10 | |
| Skype | $8 | |
| Telegram | $6 | |
| Signal | $6 | |
| Entertainment | Apple Music | $15 |
| Disney+ | $14 | |
| Netflix | $12 | |
| Spotify | $12 | |
| Hulu | $11 | |
| Twitch | $11 | |
| HBO Max | $10 | |
| Amazon Prime Video | $9 | |
| SoundCloud | $6 | |
| Other | Patreon | $7 |
| Quora | $4 | |
| Engagement x1000 | Twitter Retweets | $25 |
| Twitch followers | $12 | |
| Instagram likes | $11 | |
| Facebook likes | $8 | |
| Instagram followers | $6 |
2023 Prices for Hacked Social Media Accounts
As our list of social media channels indicates, there’s no lack of personal account data ready for sale.
Here are tables that provide the values of hacked user accounts (the more direct route to valuable personal information) and social media responses (likes, followers, and retweets).
Considering the brisk trade in personal information available on the Dark Web, it’s time to discuss how to avoid becoming part of that trade.
Hacked social media accounts
| Type | Hacked service | Price |
|---|---|---|
| Social Media | $45 | |
| | $14 | |
| | Discord | $12 |
| | $12 | |
| | Snapchat | $11 |
| | $10 | |
| | $9 | |
| | TikTok | $8 |
| | $6 |
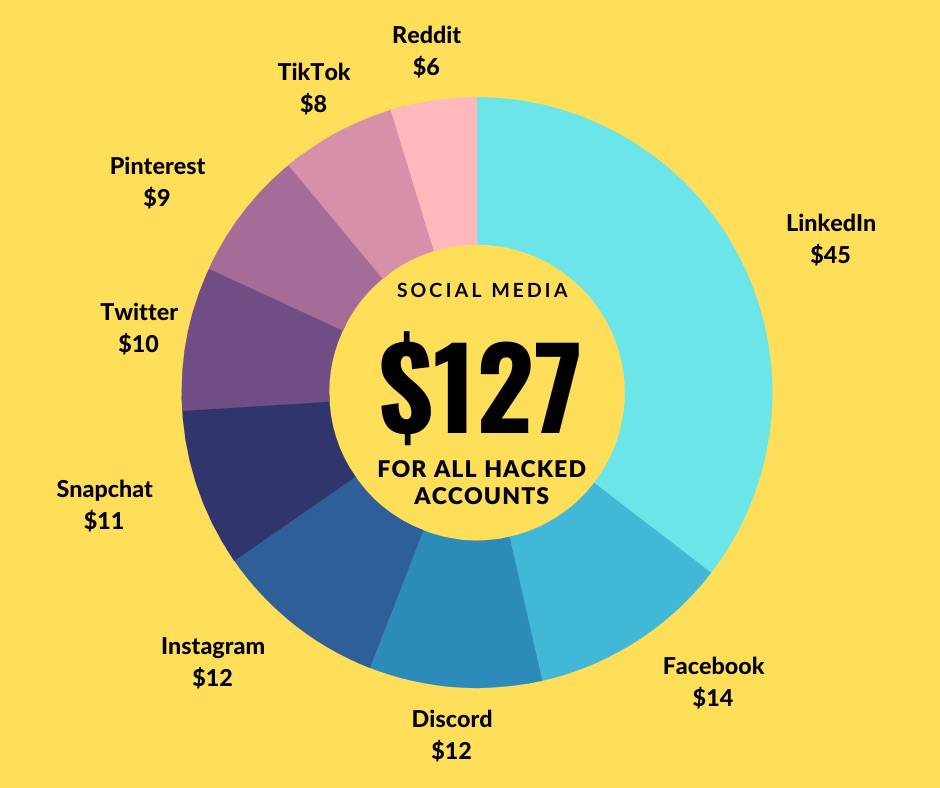
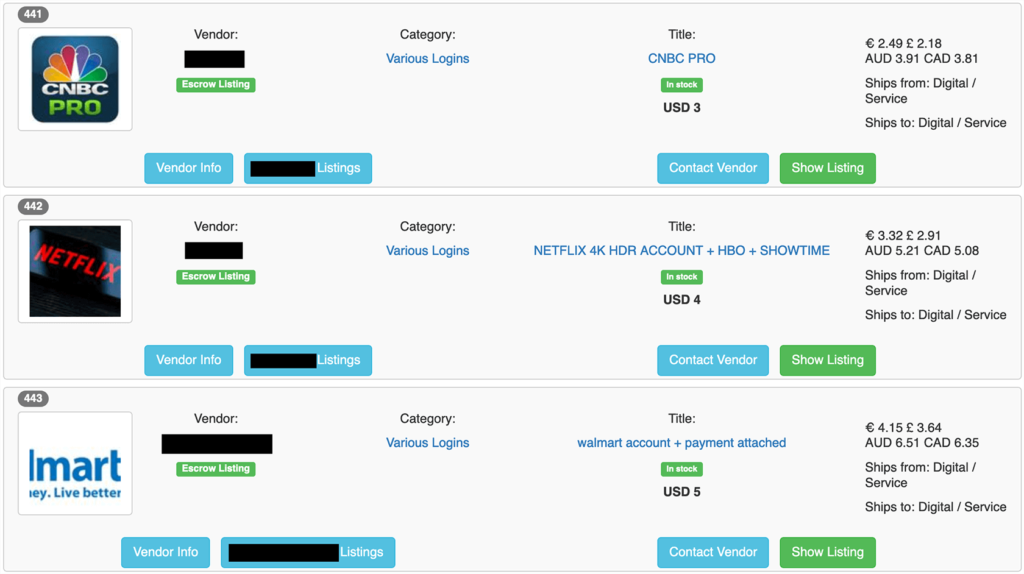
By far, the most abundantly available accounts were that of social media.
Our research found that most darknet markets have hacked social media profiles for sale. Prices can start from as low as just $6 per hacked account.
The cheapest hacked accounts were from Reddit, TikTok, and Pinterest, going for just $6, $8, and $9.
The most expensive hacked social profile appeared to be LinkedIn, which sold for around $45 per account. This is not surprising, considering that this platform caters to a professionally minded audience.
For just $127, one can buy a hacked account from all major social media networks.
This is how a typical dark web marketplace page looks like where hacked social media accounts are sold:
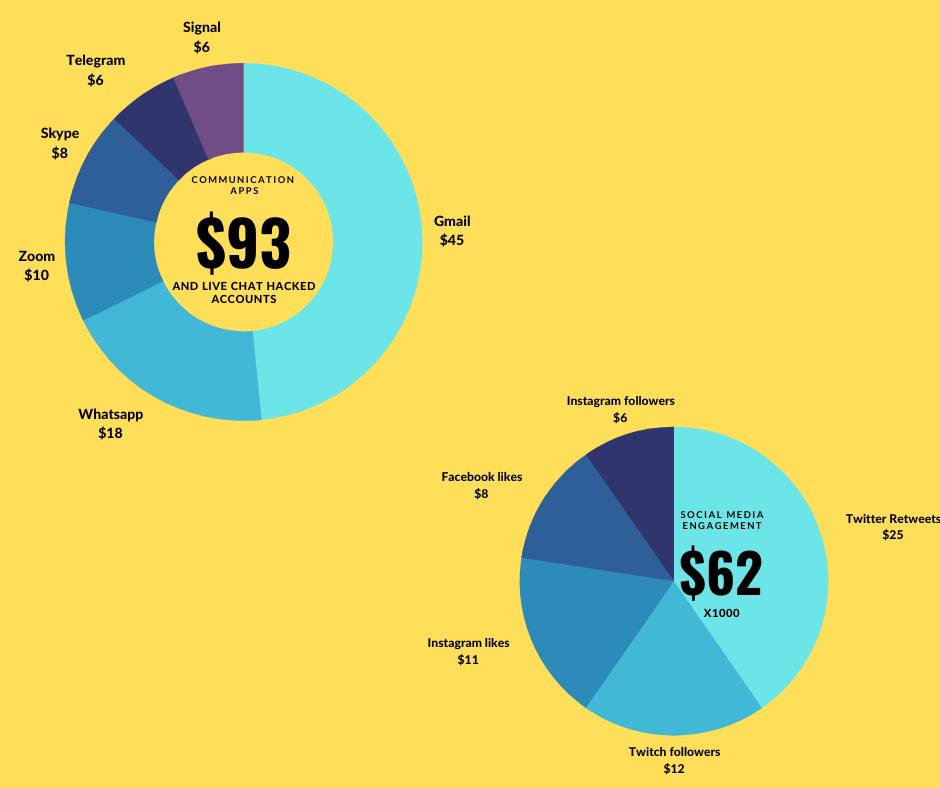
Hacked communication and live chat tools
| Type | Hacked service | Price |
|---|---|---|
| Communication | Gmail | $45 |
| | $18 | |
| | Skype | $6 |
| | Telegram | $8 |
Hacked Gmail accounts seem to be the most expensive items when it comes to communication tools. Considering that most businesses use Gmail daily, this is of little surprise.
WhatsApp, Skype, and Telegram accounts can also be obtained relatively cheaply.
This can potentially allow cybercriminals to use these accounts to reset passwords their original owners used to sign up for various services. This could include financial and payment accounts as well.
Hacked entertainment service accounts
| Type | effff9Hacked service | Price |
|---|---|---|
| Entertainment | Apple Music | $15 |
| | Disney+ | $14 |
| | Netflix | $12 |
| | Spotify | $12 |
| | Hulu | $11 |
| | Twitch | $11 |
| | HBO Max | $10 |
| | Amazon Prime Video | $9 |
| | SoundCloud | $6 |
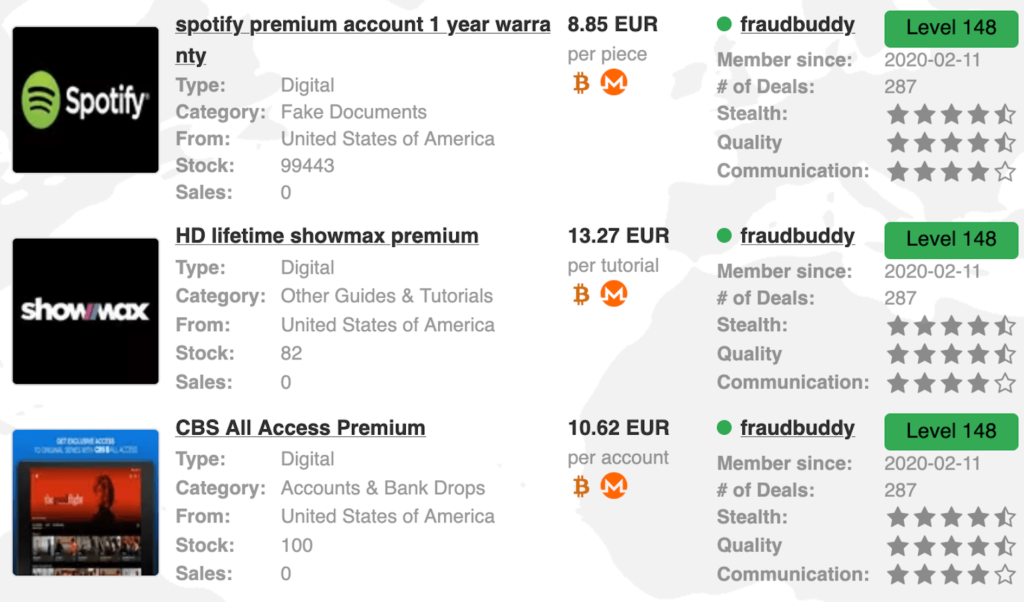
Besides social media profiles, hacked entertainment service accounts are extremely prevalent on dark web markets.
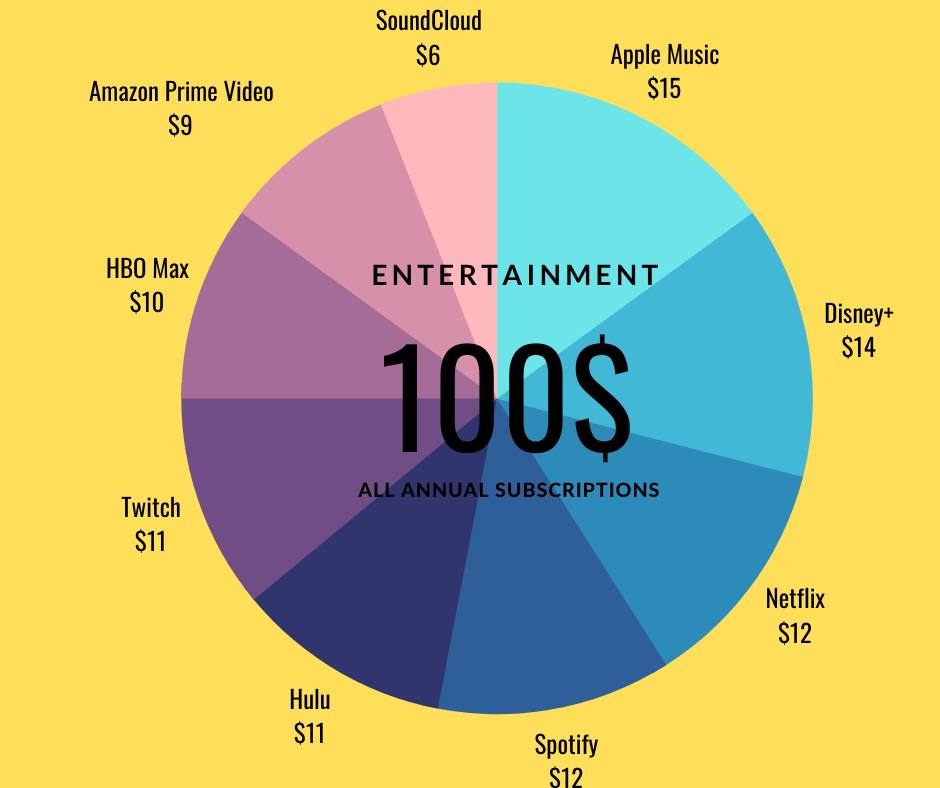
Most of these are obtained from social engineering or phishing campaigns after hackers have compromised users’ email addresses used at registration.
Usually, these accounts are linked to their original owners’ payment processing solution, which the hackers often compromise.
The original owners are locked out of these accounts, unable to unlink their card details from them. The only solution in these situations is to cancel the attached credit or debit card.
Social media engamenent
| Type | Hacked service | Price |
|---|---|---|
| Engagement x1000 | Twitter Retweets | $25 |
| Twitch followers | $12 | |
| | Instagram likes | $11 |
| | Facebook likes | $8 |
| | Instagram followers | $6 |
Instead of selling their “loot,” many hackers use the compromised accounts to run “sophisticated bot farms” for social media engagement manipulation.
The advantage of this versus setting up direct bot accounts is that the hacked accounts originally belonged to real people, meaning that the manipulation campaigns will be much harder to detect by social networks.
Our research shows that buying social media engagement is extremely cheap. For just $25, one could buy 1,000 Twitter retweets from seemingly legitimate accounts.
For just $8, one could buy 1,000 Facebook likes on a page or a post.
It is often possible to choose the country of origin for the Likes or retweets for a few extra bucks.
This again shows that one should always be cautious when looking at popular or highly engaging things on social media. For the price of a hot dog, someone could make a profile look more popular than it is.
Social Media and Entertainment Account Security Matters
Keeping social media and entertainment software accounts secure reduces social disruption, identity fraud, and outright theft.
Keeping social media and entertainment accounts safe and private is a good idea.
The Impact of Social Media and Entertainment Software Hacks
What’s the harm in social media and entertainment software cyberattacks? Quite a bit. Criminals can use cybercrime exploits or social media campaigns to:
- Spread misinformation. This high-impact result of cybercrime shows why preventing social media cybercrime is more important than ever. Cyberattackers can use social account information to target you for organized misinformation campaigns, which can have personal, financial, or political consequences.
- Cyberattackers are creative. They can scam or rob you for money or gaming tokens. By combining personal information gathered from your social media accounts, they’ll ply you with opportunities to support Ukrainian orphans or health crisis-burdened single parents.
- Steal your money. Not only do you lose funds, but it often occurs without your knowing that anything happened. Fraud and scams can also include outright theft enabled by lax security of bank and credit card accounts.
- Steal your identity. After breaching your personal account information, attackers will go on a spending spree or commit crimes in your name.
How to know if you’ve been hacked?
There are plenty of indicators of getting hacked. The most familiar ones include:
- Getting a ransomware message.
- Getting a fake antivirus message.
- Viewing unwanted browser toolbars.
- Your browser constantly redirects you to internet searches you didn’t start.
- Being bothered by frequent, random popups.
- Your friends tell you that they receive social media invitations from you. The problem is, you didn’t send an invitation.
- Getting frustrated—your online password isn’t working.
Protecting yourself from social media data disruption?
Protecting yourself and family members from social media data thievery resembles the basic principles designed for businesses.
You’ll find many of the same best practices listed for both groups. This overlap encourages security professionals, social media, and entertainment software users to develop a cautious (some would say cynical) approach to cybersecurity. Here are three thoughts to go by:
- First, remember that cybersecurity is a numbers game. It’s about reducing risk (a number between 0 and 1) as much as possible.
- Next, assume that digital footprints—cyber crooks, hackers, and bad actors—are everywhere. You’ll never eradicate those footprints. So, accept that total safety in cyberspace doesn’t exist.
- Finally, this vulnerability proves that there will always be a need to verify access requests and confirm that they are authenticated and authorized. So, try to use the effective best practices and authentication tools you can find.
How to reduce the risk of data disruption?
Ransomware, identity theft, and other crimes become more common as social media networks become more important to our daily lives.
Simple mistakes can compromise your personal information, allowing scammers to steal your identity and use your Social Security number or damage your credit.
Active social media users are 30% more likely to be affected by identity fraud.
Maintaining your identity on social media is essential to protect your safety and financial health.
How to protect your social media privacy and data?
Reducing your risk of social media data disruption is largely a matter of common sense. (Notice that we didn’t say that these or any practices prevent an attack, (That isn’t possible.) But it’s also a matter of remembering that common sense when needed.
However, you can use these practices to reduce the risk of attack. Here are the social media practices most likely to keep you out of trouble:
- Keep all personal information private. This year’s Javelin online security report studied social media user behavior. Researchers discovered that more than two-thirds of people with public social media profiles shared birth dates or other highly personal data. It’s safer to omit information in your social media apps. For example, provide regional information (Greater Detroit Area ) instead of your city. This approach provides helpful information (when people want to figure out your time zone). But it’s harder to learn your home address or ZIP code.
- Set strict privacy settings. Go into the Settings section of your Facebook, Twitter, Pinterest, Instagram, and LinkedIn apps to edit your privacy settings. Ensure all your personal information is private or visible only to your family and friends.
- Know your friends and connections. Don’t make yourself or your information vulnerable to people you have never met. Befriending people you haven’t met makes it easier for them to use the information on your social media to find out more about you. Don’t be reluctant to decline a friend request from a stranger.
- When you finish a session, always log out of social media. This is especially important when using a public computer, such as a library or hotel.
- Use an internet security software suite. Get antivirus software that includes secure environments, identity theft protection, malware detection and removal, and encrypted password protection.
And what about scams, a perennial favorite of hackers?
Watch out for scams
Recent scams have shifted from email phishing to account fraud. These are some common schemes:
- Impersonation: When hackers get hold of some of your personal information, they can message friends of the compromised account holder and ask for favors. Some messages may be innocuous, asking your friends about your weekend plans or work hours to learn when your home will be vacant. Others are more overt. These messages might claim that your friend is in s trouble and urgently needs money. Never consider sending money without verifying that the request is genuine. A phone call or text message should clear up any mystery.
- Quizzes: Many quizzes ask questions about the street of your childhood home, where your parents were married, or the name of your first pet. Posting your filled-out questionnaires offers potential hackers an easy opportunity to learn your passwords.
- Business opportunities: Remember one rule: Don’t pay for anything upfront when looking into employment opportunities. Often, someone sends you a message promising a starter kit to help you in your new career as a salesperson. But first, of course, you need to provide your credit card information… No. No. Never.
We hope that the data presented in this research and the guide will aid you in avoiding getting scammed online or stealing your personal data.
Stay safe!





Hello Alex, Can you help me for know my wife Instagram password?